Introduction
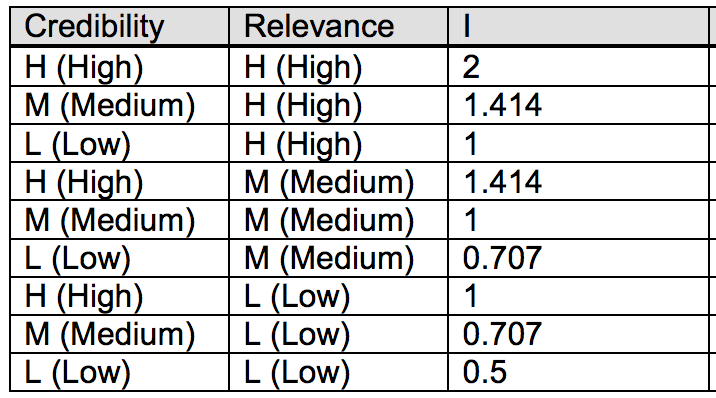
In my previous diary, I did a very brief introduction on what the ACH method is [1], so that now all readers, also those who had never seen it before, can have a common basic understanding of it. One more thing I have not mentioned yet is how the scores are calculated. There are three different algorithms: an Inconsistency Counting algorithm, a Weighted Inconsistency Counting algorithm, and a Normalized algorithm [2]. The Weighted Inconsistency Counting algorithm, the one used in today’s examples, builds on the Inconsistency algorithm, but also factors in weights of credibility and relevance values. For each item of evidence, a consistency entry of “I” counts -1 against the corresponding hypothesis. Then, Credibility and Relevance are weighted as follows: L (Low) is assigned the value 0.707, M (Medium) is assigned the value 1, and H (High) is assigned the value 1.414 and then weight values are multiplied together to determine the aggregate weight for a each piece of evidence. The default table looks like the following:
Today, I will apply ACH to a recent quite known case: WCry attribution. There has been lots of analyses and speculations around it, lately several sources in the InfoSec community tied WCry strongly to Lazarus Group [3][4][5][6], while some others provided motivation for being skeptical about such attribution [7]. Therefore, it is a perfect case to show the use of ACH: several different hypotheses, facts, evidences and assumptions.
Digital Shadows WCry
ACH analysis About two weeks ago, Digital Shadows published a very well done post on ACH applied to WCry attribution [8]. Regarding possible attribution to Lazarus though, as stated on their post, “At the time of writing, however, we assessed there to be insufficient evidence to corroborate this claim of attribution to this group, and alternative hypotheses should be considered.” Therefore among the hypotheses considered is missing one specifically for Lazarus in place of a more generic “nation state or state affiliate actor.” The following are the four different hypotheses considered by Digital Shadows:
- A sophisticated financially-motivated cybercriminal actor - H1
- An unsophisticated financially-motivated cybercriminal actor - H2
- A nation state or state-affiliated actor conducting a disruptive operation - H3
- A nation state or state-affiliated actor aiming to discredit the National Security Agency (NSA) – H4
Plenty of evidences where also considered and the final ACH matrix resulted is the following:
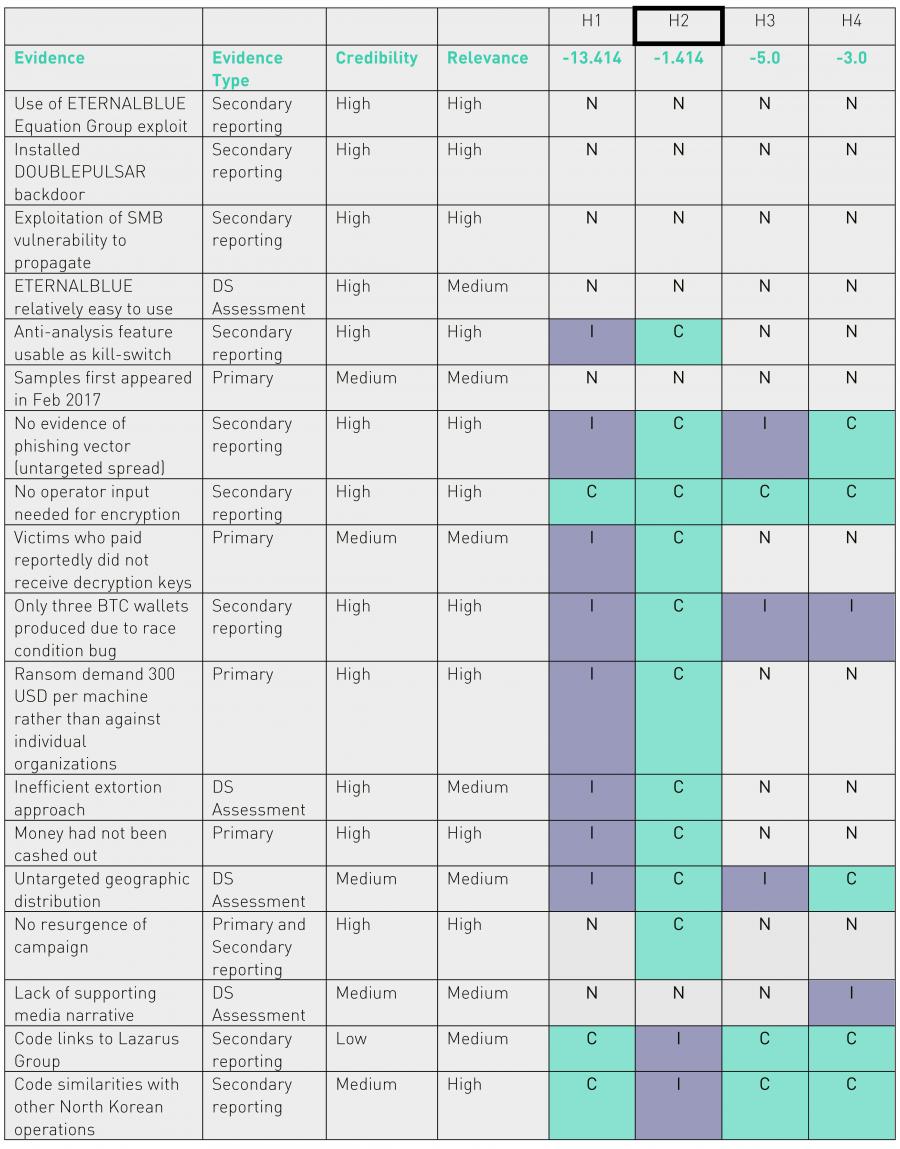
Given the final scores computed, they have assessed that "though by no means definitive, a WannaCry campaign launched by an unsophisticated cybercriminal actor was the most plausible scenario based on the information that is currently available." Just one note on my side, from my calculation seems they have made a mistake, and H2 score should be -2.121 rather than -1.414. This does not change the final result, but brings H2 and H3 way closer.
My WCry ACH Analysis
Although the Digital Shadows analysis was a very good one, I felt something was missing, both on the hypotheses as well as on the evidences side. Particularly, in my opinion, I would add three more hypotheses.
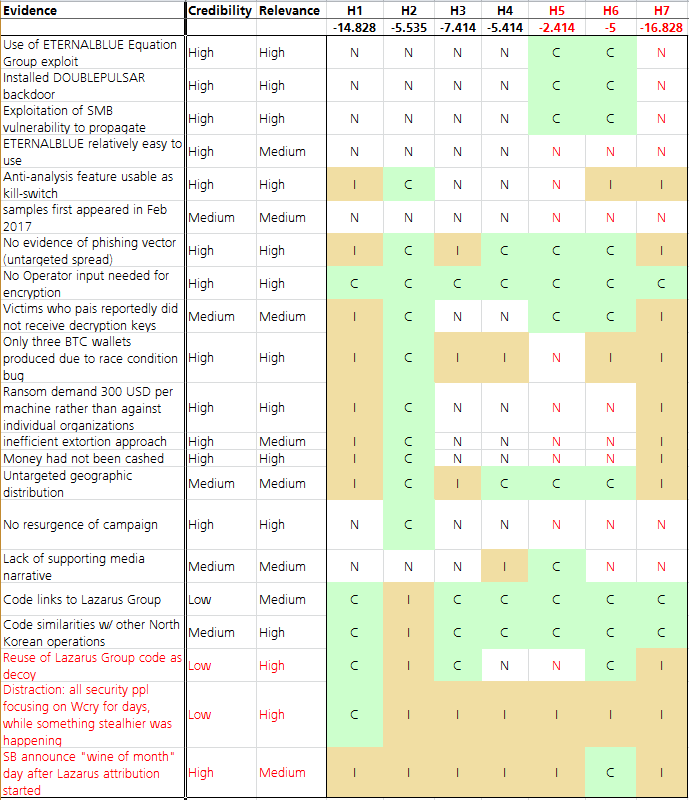
When thinking about NSA being the final target of this, other than A nation state or state-affiliated actor aiming to discredit the NSA, I think that it should be considered also a (generic/unattributed) TA aiming at unveiling/exposing the extent of possible NSA network of compromised machines (H5). This is something one would expect from a hacktivist maybe, although it seems to be way more sophisticated than what hacktivist have got us used to. One difference with the H4 could be on the lack of supporting media narrative. While if one wants to discredit NSA would be ready to have a supporting media narrative, if the goal was simply to unveil and show to everyone the potential extent of NSA infected machines, the infection as it was would have been sufficient, given also the abundant media coverage it got. Although this may still be seen as too close to H4 to be a different hypothesis, I still do see a case for it.
The other hypothesis I’m considering is Shadow Brokers being behind it (H6). This because they had collected some big failures in the previous attempts of monetizing their dumps, as apparently not much credit was given to them or to the quality of their claims. The WCry incident proved the high quality of their leak. As one of the arguments for this, by timely coincidence as soon as the first Lazarus attribution started to come up, SB announced their “data dump of the month” service [9]. How many people will now think more about buying their offer?
Finally, I believe a specific hypothesis for Lazarus, other than generic nation state actor, is needed given the number of reports and evidence attributing WCry to it (H7). If I consider Lazarus, I consider financial gain as the motivation behind it, since historically this has been its focus and the ransomware is indeed a lucrative market. However, H7 would be inconsistent with the failed of decrypting after ransom was paid. This does not serve as good advertisement, and fewer victims would start paying once the rumor that files won’t be decrypted anyway spreads. Another inconsistency point for me would be the race condition bug related to the BTC addresses, given the quality of the Lazarus code we are used to. But I may be missing something here.
Also on the side of the evidences, in my opinion, there was missing some important pieces. First is the assumption of code reuse for deception purposes. Code reuse is way too probable, it happens all the times and its use as decoy cannot be ignored as one of the possibilities. Secondly, as also commented by others in the community, the element of distraction: while all security folks were chasing WCry, something else much stealthier was happening. While this maybe seen as rare event, it does happen and, again, is something to consider given the events.
The following is the resulting ACH matrix, with in red the new hypotheses and evidences I have added compared to Digital Shadows analysis.
Conclusions
While from the results above there seems to be a clear winner in H5, (generic/unattributed) TA aiming at unveiling/exposing the extent of possible NSA network of compromised machines, what I see in cases like this are three clear “losers”: H1, a sophisticated financially motivated attacker, H3, a nation state or state-affiliated actor conducting a disruptive operation, and H7, Lazarus Group. I would then focus on looking for other elements with regards to the hypothesis that are left in the refinement face.
Given that ACH is done better when multiple analysts contribute with their views, please share your feedback. As stated by the guys at Digital Shadows too, also my analysis is by no means definitive.
Finally, I’m sharing my Excel template I made and use to do ACH, for those who would like to experiment with it. You can find it here https://github.com/pstirparo/utils/blob/master/ACH_template-v0.4.xlsx
Happy Hunting,
Pasquale
References:
[1] – P. Stirparo, “Analysis of Competing Hypotheses (part 1)”, https://isc.sans.edu/forums/diary/Analysis+of+Competing+Hypotheses+ACH+part+1/22460/
[2] – Palo Alto Research Center, “ACH1.1: A Tool for Analyzing Competing Hypotheses”; http://www.pherson.org/PDFFiles/ACHTechnicalDescription.pdf
[3] – Neel Mehta, https://twitter.com/neelmehta/status/864164081116225536
[4] – Kaspersky, “WannaCry and Lazarus Group – the missing link?” https://securelist.com/blog/research/78431/wannacry-and-lazarus-group-the-missing-link/
[5] – Symantec, “WannaCry: Ransomware attacks show strong links to Lazarus group”; https://www.symantec.com/connect/blogs/wannacry-ransomware-attacks-show-strong-links-lazarus-group
[6] – BAE Systems, “WanaCrypt0r RansomWorm”; https://baesystemsai.blogspot.ch/2017/05/wanacrypt0r-ransomworm.html
[7] – ICITech, “There's Proof That North Korea Launched the WannaCry Attack? Not So Fast! - A Warning Against Premature, Inconclusive, and Distracting Attribution”; http://icitech.org/theres-proof-that-north-korea-launched-the-wannacry-attack-not-so-fast-a-warning-against-premature-inconclusive-and-distracting-attribution/
[8] – Digital Shadows, “WannaCry: Analysis of Competing Hypotheses”; https://www.digitalshadows.com/blog-and-research/wannacry-an-analysis-of-competing-hypotheses/
[9] – The Shadow Brokers, “OH LORDY! Comey Wanna Cry Edition”, https://steemit.com/shadowbrokers/@theshadowbrokers/oh-lordy-comey-wanna-cry-edition
Pasquale Stirparo, Ph.D. @pstirparo
from SANS Internet Storm Center, InfoCON: green https://isc.sans.edu/diary.html?storyid=22470&rss
via IFTTT
Comments
Post a Comment